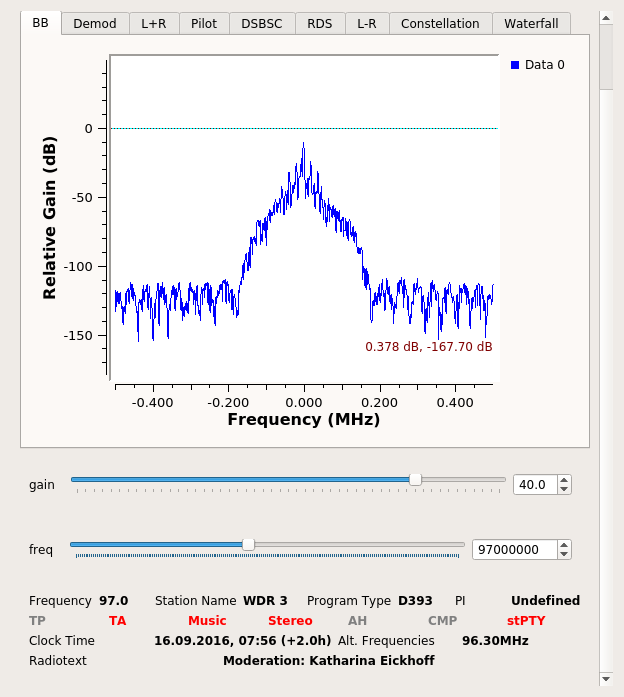
Over at Twitter, Joseph Redfern came up with a nice application for my GNU Radio receiver for wireless car key fobs.
Recently, I had a hard time compiling the GNU Radio next branch on macOS.
The main problem is that next switched to QT5, which uses QWT6 for plotting.
Unfortunately, QWT6 is not yet available in Homebrew, but has to be installed manually.
Compillation is rather straight forward, but there are several pitfalls:
- GNU Radio searches for a package config file for QWT6.
This is not created by default and has to be configured in
qwtconfig.pri.
- QWT installs itself as a
framework, which is a special type of shared library on macOS.
This doesn’t work for GNU Radio as it uses the QWT_LIBRARIES variable in cmake, which is not set for a framework.
That means you will have to edit the package config file and replace the framework config with a corresponding shared library configuration.
(This also requires adapting libdir and includedir.)
# old
Libs: -F${libdir} -framework qwt
# new
Libs: -L${libdir} -lqwt
- GNU Radios cmake config does not support setting the library with
-lqwt and adding its path to the shared library search path with the -L switch.
Instead, I had to add the full path to the library with
Libs: -L${libdir} -l${libdir}/qwt
- The last problem was that QWT did not set its install name to its full path. While there is a configuration option especially for that, it did not work for me. I had to manually change the library name with
install_name_tool -id '/Users/basti/usr/.../qwt' qwt
Hope it helps.
…aaand it’s gone. The WX GUI was recently deleted in GNU Radio’s next branch.
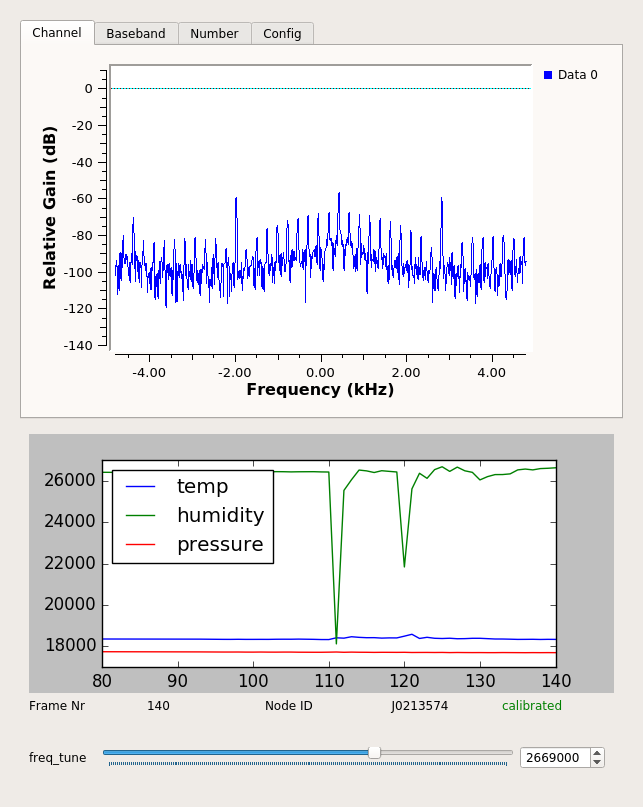
I just finished porting all my modules to QT.
For the weather balloon receiver and the RDS transceiver, it was a bit tricky since I use custom panels.
They now look like this:
Please let me know if there are problems.
I just wanted to give a brief update of my key fob project.
Maybe you remember that, following a recent paper, it seems as if the firmware of VW ECUs contains a master key that can be used to clone arbitrary keys by overhearing a single transmission.
I already blogged about that earlier.
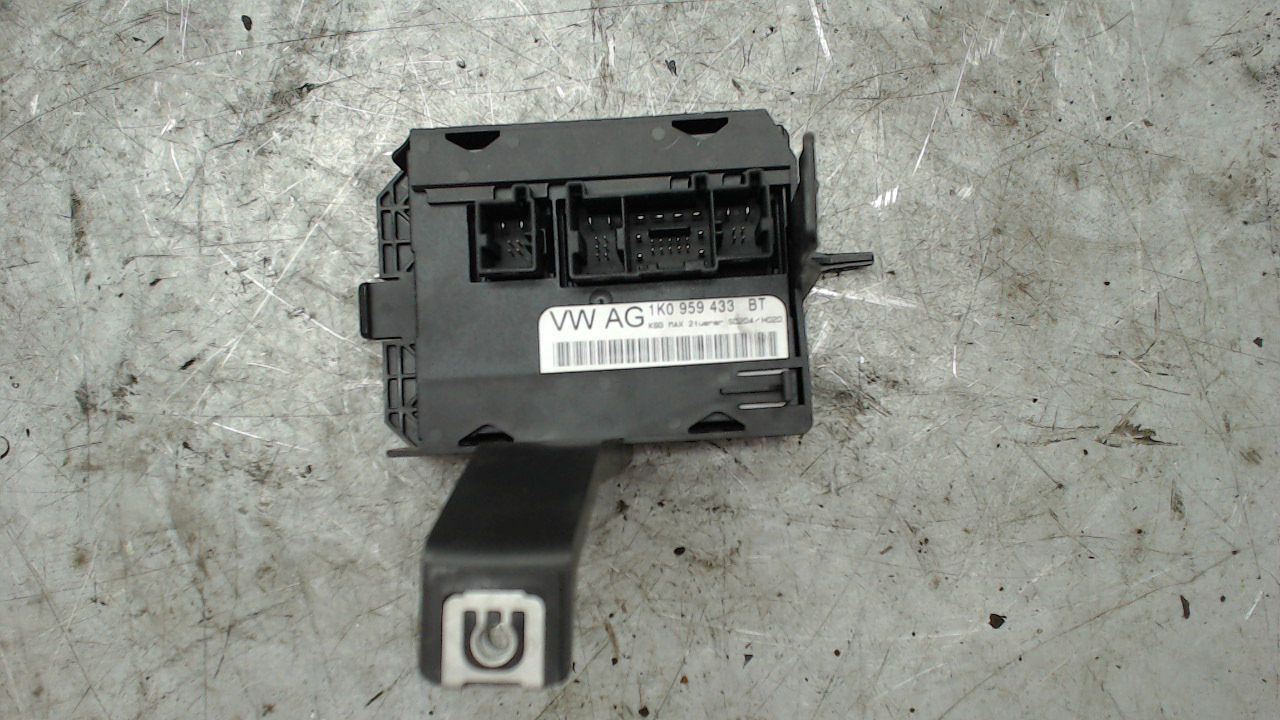
In the meantime, my Comfort Control Unit arrived.
I’m pretty confident that this is the ECU in question since it’s also made by Hella, the company that sells the keys.
Here are some photos from the board.
read more
Today, I was happy to merge pull-request from Jonathan Brucker that added RFtap support to some of my OOT modules.
RFtap bridges the gap between SDR transceivers and network monitors like Wireshark.
In a nutshell, it reads metadata (like encoding, SNR, or frequency offset) from the receiver and makes it available to the monitoring software.
What’s really great is that RFtap can be extended with custom dissectors.
In this blog post, Jonathan describes how he connect my gr-rds transceiver to Wireshark.
Note that while there is something very similar available for WiFi (the Radiotap header), RFtap is more flexible and allows adding more fine-grained information.
I’ve recently seen a great video where a student gave a brief overview of his paper.
I think it’s very nice to have this executive summary as an ad for the paper.
So, of course, I wanted to give it a try.
Strangely, I found it way, way harder than expected.
Looks like giving a monologue to myself is something I am not used to.
So here is what I came up with.
Good thing is, it leaves much room for improvements :-)
-
 Bastian Bloessl, Mario Gerla and Falko Dressler, “IEEE 802.11p in Fast Fading Scenarios: From Traces to Comparative Studies of Receive Algorithms,” Proceedings of 22nd ACM International Conference on Mobile Computing and Networking (MobiCom 2016), 1st ACM International Workshop on Smart, Autonomous, and Connected Vehicular Systems and Services (CarSys 2016), New York, NY, October 2016.
[DOI, BibTeX, PDF and Details…]
Bastian Bloessl, Mario Gerla and Falko Dressler, “IEEE 802.11p in Fast Fading Scenarios: From Traces to Comparative Studies of Receive Algorithms,” Proceedings of 22nd ACM International Conference on Mobile Computing and Networking (MobiCom 2016), 1st ACM International Workshop on Smart, Autonomous, and Connected Vehicular Systems and Services (CarSys 2016), New York, NY, October 2016.
[DOI, BibTeX, PDF and Details…]
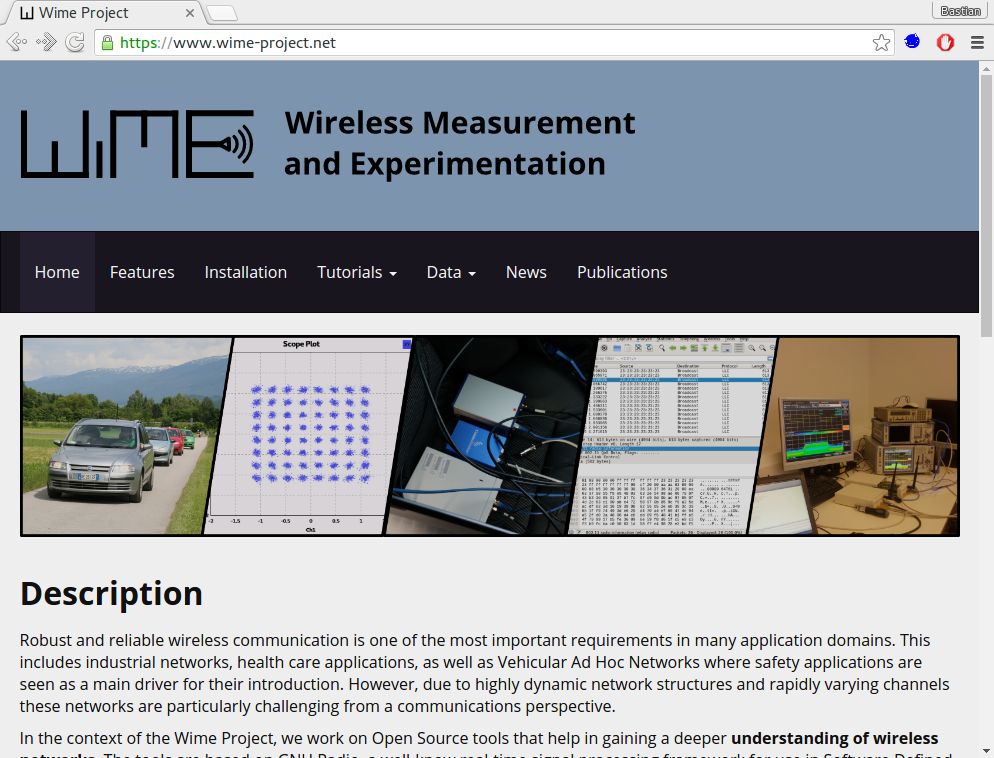
I just uploaded a new website for the Wime Project, an umbrella project for most of my work on GNU Radio OOT modules.
I also created Facebook and Twitter accounts that will keep you updated.
Today, I was very happy to read On prototyping IEEE802.11p Channel Estimators in Real-World Environments Using GNURadio by
Razvan-Andrei Stoica, Stefano Severi, and Giuseppe Thadeu Freitas de Abreu, presented at 2016 IEEE Intelligent Vehicles Symposium (IV).
The paper extends my GNU Radio WiFi transceiver with another state-of-the-art channel estimation algorithm, designed specifically for Vehicular Ad Hoc Networks.
I’m particularly happy, since I always hoped to motivate exactly this kind of papers by releasing the software under an Open Source license.
Apart from the algorithm itself, the authors also implemented well-established channel models for vehicular networks.
I already dropped them an email and hope I can motivate them to contribute their code.
It would be really great to have it in the module.
During the last days, I was happy to see that normal news covered findings from wireless security researchers, who reverse engineered many wireless car key fobs from the VW group, unveiling major security issues.
This Wired article, for example, gives a good overview.
The critical point is that VW uses very few master keys to encrypt the data sent by the key.
Once these master keys (which are deployed in every key fob and every car) are disclosed, it’s trivial to clone keys by overhearing the signal from a single key press.
The results were published in the paper Lock It and Still Lose It – On the (In)Security of Automotive Remote Keyless Entry Systems by Flavio D. Garcia, David Oswald, Timo Kasper, and Pierre Pavlidès, which was presented at 25th USENIX Security Symposium.
It covers many wireless car key fobs, including the ones that I had a look at.
My GNU Radio transceiver supports the keys that are referred to as VW-3 and VW-4 in the paper.
Both versions use the same physical layer and frame structure, but differ in the algorithm used to encrypt the data.
As far as I understand, the authors didn’t omit any information on that part of the system.
So that seems to be settled.
The only thing that’s still unclear is how to acquire the master key.
In the paper, the authors state that they extracted it from one of the car’s Electronic Control Units (ECUs).
However, to me, it seems that this part requires another trick.
When talking about key extraction, the authors mention:
Note that as part of our negotiations with VW Group, and to protect VW Group
customers, we agreed to not fully disclose the part
numbers of the analyzed ECUs and the employed
μCs at this point. We furthermore agreed to omit
certain details of the reverse-engineering process, as
well as the values of cryptographic keys.
After some discussions with a friend, I think the ECU in question is the Comfort Control Module (Komfortsteuergerät), which sells for about 30 EUR on Ebay.
I read in several forums that it contains the receiver for the wireless key fob.
Furthermore, it is manufactured by Hella, who also sells the keys.
So that makes, at least, some sense.
I just bought one of those ECUs for my Skoda Octavia.
Since it looks like the same module is used with models from 2006 to 2012, I think that it might still use the VW-3 encryption scheme.
Looking forward to having a look in the box.
Procrastinating writing my thesis, I seem to come up with all kinds on nonsense.
This one, however, is actually important.
It’s about the feeling I get when reading other people’s thesis.
They all seem to have this deep, intellectual quotes at the start of every chapter.
Every time I see somebody citing Plato, I wonder, how the heck did that guy manage to write his thesis, while catching up with the philosophical body of literature, dating back before Christ.
I’m not that kind of guy, but I also didn’t want to miss the unique opportunity to impress people by showing how intellectual I am.
So I decided for using good old fortune to insert something for me.
Currently, my chapter headers look something like:
\chapter{Introduction}
\label{sec:introduction}
\immediate\write18{./quote.sh \the\value{chapter}}
\epigraph{\input{/tmp/fortune-\the\value{chapter}}}{--- \textup{\texttt{/usr/bin/fortune}}}
This runs quote.sh for every chapter and inserts the quotes from LaTex files that it generates.
(Yes, you can run shell scripts from LaTeX (at least, if you enabled shell escape, which you probably have).
This is exactly why it’s a bad idea to compile other peoples LaTeX files without checking the sources.
If there would be something like rm -rf ~, then bye bye home directory.)
The qhote.sh script checks if there is already a fortune for that chapter.
If there is none or if it’s older than an hour, it will create a new one.
#!/bin/bash
# new fortunes every hour
if [ ! -f /tmp/fortune-$1.tex ] || test "`find /tmp/fortune-$1.tex -mmin +60`"
then
fortune | sed -e 's/-- .*//g' | sed '/^\s*$/d' > /tmp/fortune-$1.tex
fi
With this I have awesome (albeit sometimes a bit demotivational) chapter quotes in my thesis :-)
Let’s see what the next hour brings.