I just came back from some very nice days in Brussels.
On Thursday and Friday, I joined the DARPA SDR Hackfest, which was all about characterization and detection of incidental interference sources.
Unfortunately, I was one day late and missed the discussion and teaming phase.
I, therefore, did not contribute to the actual hacking, but, nevertheless, had some very nice days.
It was a great get-together and DARPA was an fantastic host.
For the hackfest, they booked the top floor of The Hotel, where we had an awesome view over Brussels.
On Saturday, there was a very dense and interesting program in the SDR DevRoom of FOSDEM 2017.
During the whole day, people were queuing in front of the door.
I also gave a short talk about me playing around with mobile wireless traffic lights.
Apart from that, I was very proud to be invited to the SDR panel on Which are the top 3 challenges for free software radio?.
I don’t know if I had much to contribute, since the other panelists were so much more experienced than me.
They were Francois Quitin (Prof. in Brussels), Ben Hilburn (Head of GNU Radio), and Tom Rondeau (DARPA Program Manager).
Anyhow, I’m very grateful for this awesome experience.
Recently, I came across Mathy Vanhoef’s amazing work on advanced WiFi attacks.
He modified the firmware of off-the-shell WiFi cards from Atheros to implement constant and reactive jamming.
Fortunately, Mathy released the code under an Open Source license and even prepared a VM with everything pre-installed.
The firmware modifications are compatible with three different types of WiFi cards, two out of which are available on Amazon and Ebay.
Of all things, the only card that supports both the 2.4GHz band and the 5GHz band seems to be very hard to get.
To implement reactive jamming he had to use a little trick:
The WiFi card consists of a transceiver chip and micro controller.
When the transceiver receives a frame it writes it to memory that is shared with the micro controller.
For reactive jamming, firmware of the micro controller is changed to busy wait for decoded data from the transceiver.
Once the first bytes are decoded, the firmware matches fields like the frame type or the MAC address to predefined patterns.
If the frame is supposed to be jammed, the firmware aborts reception and triggers transmission of an interfering frame, jamming the signal.
Of course, there is some delay between detection of the frame to sending the jam signal.
And, in fact, it turns out to be too high to jam, for example, acknowledgment frames (ACKs).
Anyhow, I found it pretty amazing that it is possible in the first place.
Furthermore, if you have fixed sized frames, it is possible to work around the limitation by detecting the data frame and delaying the jam signal until the ACK is sent.
That worked surprisingly well.
-
 Mathy Vanhoef and Frank Piessens, “Advanced Wi-Fi Attacks Using Commodity Hardware,” Proceedings of 30th Annual Computer Security Applications Conference (ACSAC 2014), New Orleans, LA, December 2014, pp. 256-265.
[DOI, BibTeX, PDF and Details…]
Mathy Vanhoef and Frank Piessens, “Advanced Wi-Fi Attacks Using Commodity Hardware,” Proceedings of 30th Annual Computer Security Applications Conference (ACSAC 2014), New Orleans, LA, December 2014, pp. 256-265.
[DOI, BibTeX, PDF and Details…]
Recently, I helped a colleague to get a basic Visible Light Communications (VLC) experiment up and running.
I was really surprised how straightforward that went.
We used two Ettus Research N210 with LFTX/LFRX daughterboards, an off-the-shelf photo diode and a custom LED driver that converts the output voltage to a corresponding current.
I tried my GNU Radio IEEE 802.15.4 transceiver and my car key fob transceiver.
Both worked out of the box.
To be honest, I’m not completely sure why O-QPSK worked – but hey, not my department :-)
Just to be clear, every time the LED switches on, it transmits a whole frame.
For IEEE 802.15.4 that was a chip rate of 2Mcps with a data rate of 250kbps.
During the last year, I was happy to serve as the Publication Chair of IEEE VNC 2016.
Since everything is done now, I wanted to write down some notes and anecdotes.
The most interesting part, for me, was to have a look behind the curtain, i.e., being in the loop when the General Chairs and the TPC discussed the conference.
Now, I have at least a bit of an idea how a conference is organized.
It was really fun to work close with people I didn’t know too good before. It was very productive and, I think, I learned a lot about professional communication.
VNC uses EDAS, a popular conference management system.
It was great to unlock some more menus and get a better understanding of how it works.
I only knew it from the perspective of an author.
However, I found the role of a publication chair to be extremely restrictive. In fact, I didn’t have the required permissions to do many of the things that people considered to be my job.
VNC is sponsored and co-organized by IEEE, but that doesn’t have anything to do with the proceedings. Conference organization and publications seem to be two separate things.
That means, the conference has still to be registered for potential inclusion in IEEE Xplore.
This is done by submitting a Conference Publication Form to apply for a Letter of Acquisition.
read more
Today, I visited the German Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik) to present some ideas for IEEE 802.11p device fingerprinting and discuss potential privacy issues in Vehicular Ad Hoc Networks.
It was a really nice and constructive meeting.
Let’s see if we can use GNU Radio and my WiFi Transceiver to extract some physical layer features from typical devices.
Let’s talk about GNU Radio’s build system, because it seems to get more and more cluttered over time.
If things don’t work, people just add stuff until it finally compiles – on Ubuntu. And maybe some other distros.
Let’s, for example, look at the includes:
include_directories(
${CMAKE_CURRENT_BINARY_DIR}
${GR_UHD_INCLUDE_DIRS}
${GNURADIO_RUNTIME_INCLUDE_DIRS}
${UHD_INCLUDE_DIRS}
${LOG4CXX_INCLUDE_DIRS}
${Boost_INCLUDE_DIRS}
)
LOG4CXX_INCLUDE_DIRS is never defined.
So some lines below someone made another attempt:
include_directories(${LOG4CPP_INCLUDE_DIRS})
It’s not added to the above list (where it would be obvious that something goes wrong), but added as a new statement.
OK. At least, we managed to included log4cpp in UHD. Makes a lot of sense, because UHD uses log4cpp, right?
Nope.
UHD uses GNU Radio runtime, which in turn uses log4cpp.
Woot?!?! But it already included ${GNURADIO_RUNTIME_INLCUDE_DIRS}.
Yes, but that’s basically just another name for gnuradio-runtime/include, i.e., the definition is not really helpful and doesn’t provide dependency tracking whatsoever.
read more
Yay! My FOSDEM talk was just accepted.
In February, I will talk about Receiving Wireless Mobile Traffic Lights.
The preliminary abstract reads like:
Wireless mobile traffic lights are often used to secure construction sites when roads are partially blocked.
Some day, when a pair of them was placed close to our home, I set off to explore how they are working.
In this talk, I will describe how I used a cheap RTL-SDR together with GQRX, Inspectrum, and GNU Radio to reverse engineer the modulation and frame format of different types of wireless traffic lights.
With some patience, I could also make some sense out of the bits.
In particular, I was able to extract the signal state and display it in a web interface, mirroring the traffic light.
A closer look at the frame format and the apparent absence of any authentication might leave one with a bit of a worrying impression regarding the security of those systems.
The days before FOSDEM, there will also be a Hackfest sponsored by DARPA.
Hope to see you in Brussels.
I love Spacemacs.
It’s by far the most awesome editor I’ve ever used.
Strictly speaking, it’s Emacs, but considering their modifications, Emacs is more the run-time environment.
Spacemacs bundles Emacs plugins to so called layers that come with a sane and consistent configuration including mnemonic key bindings.
A central layer is Evil, it brings Vim’s modal editing to Emacs.
With Evil, large parts of Spacemacs just feel like Vim, but with the extensiblity of Lisp under the hood.
(I used Vim over the last, maybe, 15 years and was super happy. But what I loved is the editing concept, not the binary.)
I tried Emacs several times in the past, but never got the hang of it.
With Spacemacs, it’s really easy to get started since it provides a complete, nicely configured environment by default.
For me, it was much easier and much more motivating to start from there than to start from scratch.
Spacemacs is really worth giving it a try.
Let alone because of Org mode, a fantastic todo list and outlining tool.
GNU Radio Configuration
When I don’t have to write stuff, I spent most of my time working with GNU Radio.
This post will be a walk-through of my configurations to make Spacemacs a nice environment to work on GNU Radio.
Layers
As I already mentioned, Spacemacs bundles plugins in layers that serve a specific purpose.
I have lots of them installed, but for C++ development the most essential are:
dotspacemacs-configuration-layers
'(helm
auto-completion
(c-c++ :variables
c-c++-enable-clang-support t
c-c++-default-mode-for-headers 'c++-mode)
cscope
git
(syntax-checking :variables syntax-checking-enable-by-default nil)
(version-control :variables
version-control-diff-tool 'diff-hl
version-control-global-margin t))
Projectile Other File
Projectile is a plugin that brings the notion of projects to Emacs.
It will look for a .git folder (or any other version control folder) in the parent directories and, if one is found, use that as the project root.
One feature of projectile is to open other files.
The corresponding header to a C++ file, for example.
We just have to tell projectile, how alternate files look.
(with-eval-after-load "projectile"
(push '("cc" "h") projectile-other-file-alist)
(push '("c" "h") projectile-other-file-alist)
(push '("h" "cc" "c") projectile-other-file-alist))
From there on, we can use ",ga" to jump to alternate files in the same buffer or ",gA" to open it in a new window.
read more
So much spectrum – so few networks.
The 5GHz WiFi band is in many areas not really utilized.
OK, it doesn’t penetrate walls as nicely as the 2.4GHz band, but that’s not always a drawback.
One reason why the 5GHz band is not as crowded as it should be, might be the fact that WiFi is only a secondary user on many channels.
These channels are allocated primarily to radars.
Maybe you already came across the term Dynamic Frequency Selection, the feature that allows a WiFi device to detect radars.
Without DFS, a device is not allow to open an access point on those channels.
The WiFi standard, however, only defines routines to migrate a network to another channel, once a radar has been detected.
The actual radar patterns are defined by a regional regulatory body.
On Linux, you can check your DFS region with:
$ iw reg get
country DE: DFS-ETSI
(2400 - 2483 @ 40), (N/A, 20), (N/A)
(5150 - 5250 @ 80), (N/A, 20), (N/A), NO-OUTDOOR
(5250 - 5350 @ 80), (N/A, 20), (0 ms), NO-OUTDOOR, DFS
(5470 - 5725 @ 160), (N/A, 26), (0 ms), DFS
(57000 - 66000 @ 2160), (N/A, 40), (N/A)
For Europe, the ETSI EN 301 893 Draft defines the actual radar patterns (see Annex D for the definition).
Once a radar is detected, an access point has to blacklist the corresponding channel for 30 minutes.
Of course, I wanted to emulate a radar and see whether the APs move away.
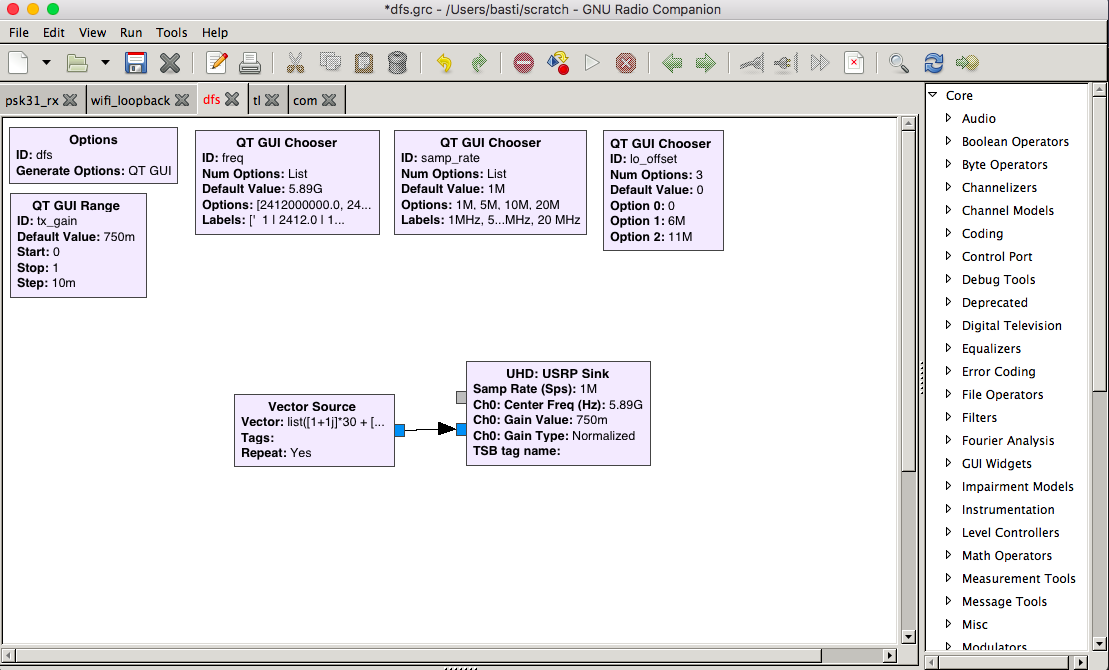
“Implementing” these radar patterns in GNU Radio is as simple as it can be.
A flow graph like this is already enough.
The vector source can be used to create the radar pulses with something like:
I tried the above flow graph with a B210 and a 6dBi dipole in the hall way of our institute.
Worked pretty well, i.e., I managed to push away many networks from DFS channels.
By the way, macOS comes with a pretty nice tool to scan for WiFi networks.
You can access it by alt-clicking the WiFi symbol in the task bar.
This will open an extended menu, where you can click on Open Wireless Diagnostics.
Then, Window → Scan will open the tool.
You can see the tool in a brief video, where I’m poking some University networks around.
Recently, they placed a pair of wireless traffic lights right in front of our university.
Today, I had the time to have a brief look.
Very convenient to put them close to eduroam and coffee :-)
Turns out, they use the same frequency band as the traffic lights that I studied earlier (around 170MHz), but use a different modulation and frame format.
Recording the signal with GQRX and loading it in Inspectrum, revealed a kind of FM in FM modulation, similar to AFSK.
The inner FM signal is 1200 baud, altering between 1200Hz and 1800Hz.
Extracting the preamble is straightforward thanks to Inspectrum.
Once the preamble is known, GNU Radio will help us to demodulate the data.
This time, I though I do a quick recording, showing how I use vim to reverse the frame format.
The work flow, described in a previous post, allows me to easily switch between offline signal processing and a live receiver.
So creating a web GUI with live updates was basically no effort.
The light was pretty bad this morning, so I couldn’t record a nice video.
Here is the one from the last year in case you are interested; it’s the very same setup.
Update
A (shaky) video of the new traffic light.